I’m Martin and I’m a Cyber-Security Engineer at N4Engage. What does a Cyber-Security Engineer do? Well, we design and build the security systems that protect N4Engage’s customers and their data, by detecting attacks and anomalies across networks and systems we can identify threats and mitigate them before they become a risk to your business.
Recently, we were reviewing our processes for alerting on security events and we realised just how many emails we were receiving and how difficult it can be to find the signal amongst all the noise. When we started to look at alternatives, our Team Collaboration solution seemed the obvious answer and when I looked into how to go about building ‘bots’ on Webex, it turned out to be remarkably simple.
I based my bot on this excellent code from hpreston on GitHub which handles all of the basic integrations automatically. First step was to get the code able to receive and respond to simple messages sent to it.

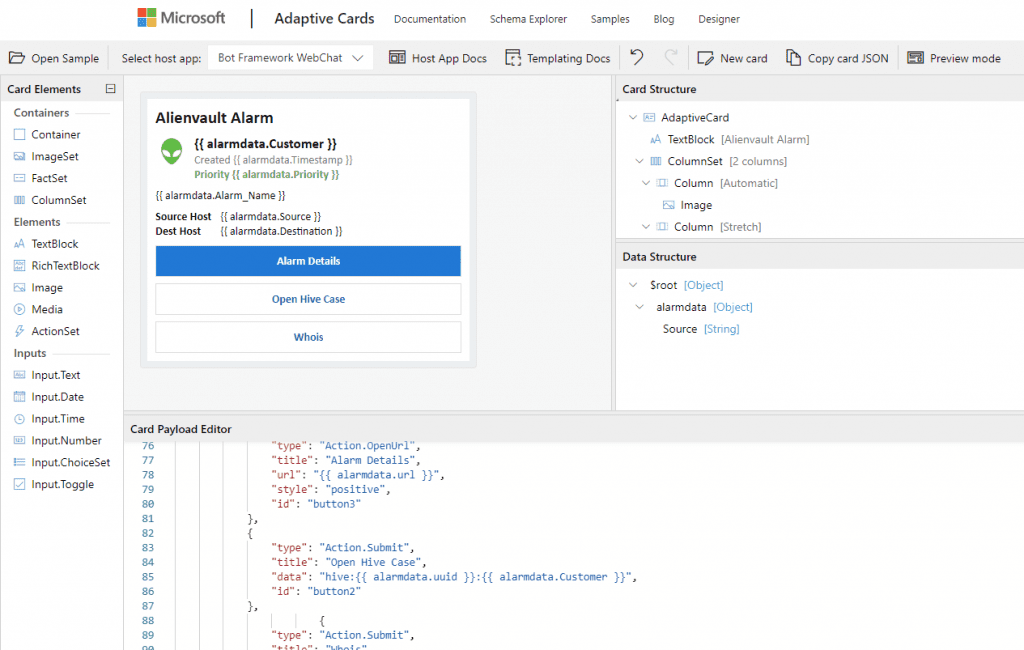
In order to format the alerts in a better way than simple markdown I used the Adaptive Cards functionality in Teams. It lets you create a card layout which is expressed as JSON – fortunately Microsoft provide a handy card designer.

Next, I needed to get messages from our SIEM platform into the bot, we primarily use Alienvault USM Anywhere for SIEM and it offers AWS SNS as a notification option however instead of triggering a Lambda function I opted to use a HTTPS webhook subscription which called directly to the python flask application running on the server.
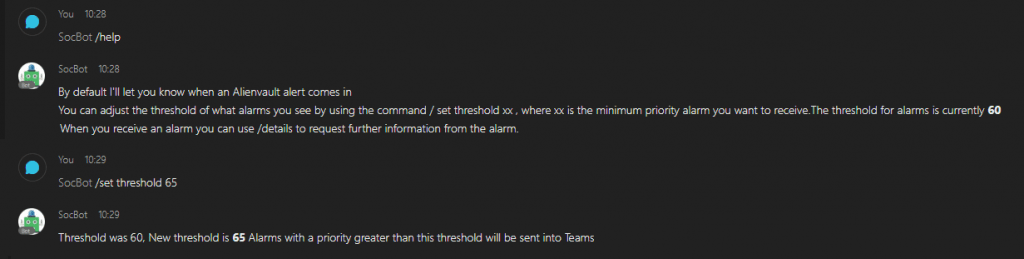
When I began my new script I started getting a lot of alerts through for low severity alarms that we don’t typically need to alert on. By including these alarms in my bot we were going to end up back where we started with alert-fatigued SOC analysts, so I added a configurable threshold for alerts and a command to update this threshold.

Next feature I wanted to add was some useful actions that could be executed directly from the Teams interface without needing to open up the SIEM console to begin investigations. After some discussion I realised these would probably look different for different kinds of alarm so I split out Office365 alarms, network intrusion alarms and malware detections to different templates. The action buttons on the cards can either link directly to a URL that will open up in the browser or can trigger a webhook within my application – the “View Alarm Details” button will open up the SIEM view, whereas the “Whois” button will trigger a whois function in my code, which grabs the relevant details and replies back to the user in the same chatroom.
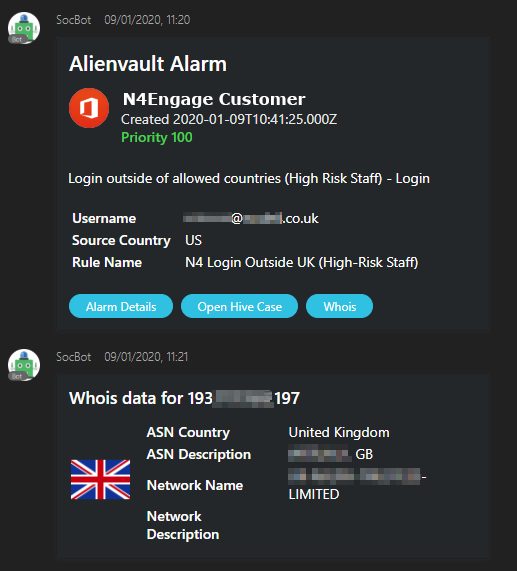

In the N4Engage Security Operations Centre (SOC), we use a security incident response platform called TheHive to track active security incidents and the indicators associated with them. In order to make it easy and frictionless to create new incidents I wanted to add a button for this too. Fortunately there’s a convenient Python API client for TheHive too which makes this a straightforward integration.
When an analyst clicks the Hive Case button in Teams, they will get a link sent back from the bot with a link to their newly created case which is automatically tagged with the correct customer and has the domains/IP addresses from the alarm added as observables.

Since we started using this new tool, we’ve found we can start investigations into high-severity incidents faster and collaborate more effectively on the analysis as a team even when we’re working remotely or on mobile devices. We’re already looking at integrating more of our systems into SocBot and improving filtering and deduplication to reduce alert fatigue while improving incident response times.
If you would like to find out more about our Security and Compliance offerings get in touch.




